In the highly regulated and data-driven domain of financial services, ensuring the security of sensitive information is paramount. With cyber threats growing more sophisticated, financial institutions face mounting pressure to safeguard their data assets. The consequences of data breaches in this sector can be catastrophic, leading to significant financial losses, legal repercussions, and damage to reputation. As such, robust data security protocols are essential to mitigate risks and protect both the organization and its customers.
The Evolving Threat Landscape
The financial services industry is a prime target for cybercriminals due to the wealth of sensitive information it handles, including personal identification details, financial records, and transaction data. The rise of digital banking, mobile payments, and online trading platforms has further expanded the attack surface, making it more challenging to secure these systems. Cyber threats such as phishing attacks, ransomware, and advanced persistent threats (APTs) have become more prevalent, targeting vulnerabilities in both legacy and modern IT infrastructures.
To combat these threats, financial institutions must adopt a proactive approach to data security, implementing comprehensive protocols that address both existing and emerging risks.
Key Data Security Protocols
Encryption
Encryption is a fundamental data security protocol that ensures data is unreadable to unauthorized users. Financial institutions typically employ encryption to protect data both at rest (stored data) and in transit (data being transmitted across networks). Modern encryption algorithms, such as Advanced Encryption Standard (AES), are essential for safeguarding sensitive financial information, such as account numbers and transaction details. Encryption helps mitigate risks by ensuring that even if data is intercepted or stolen, it remains inaccessible without the decryption key.
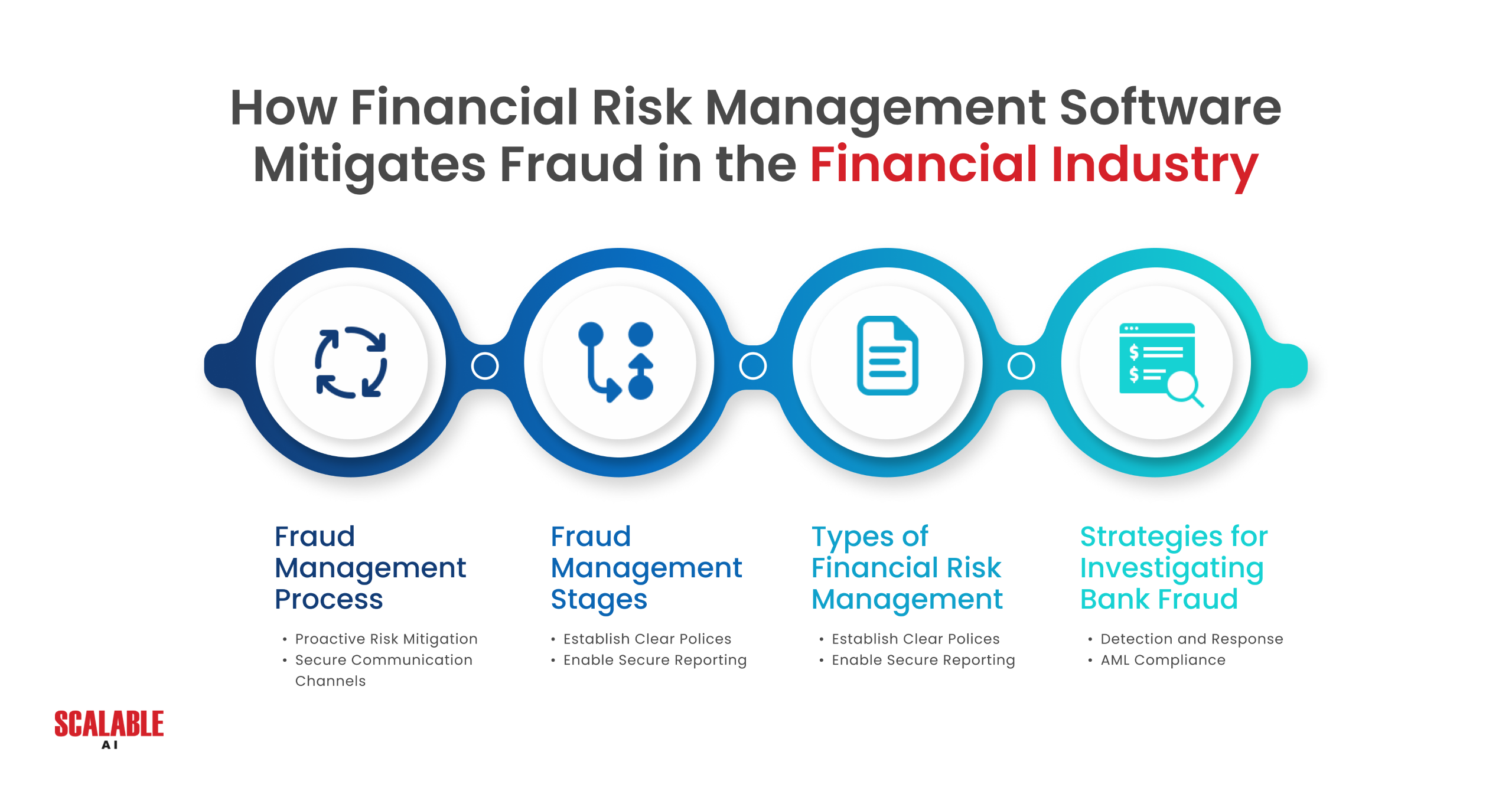
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an additional layer of security by requiring users to verify their identity using two or more authentication factors. These factors typically include something the user knows (e.g., a password), something the user has (e.g., a security token), and something the user is (e.g., biometric data). By implementing MFA, financial institutions can significantly reduce the risk of unauthorized access, particularly in cases where passwords are compromised.
Data Masking
Data masking involves obfuscating sensitive data elements, such as credit card numbers or Social Security numbers, to prevent unauthorized access while allowing the data to remain functional for certain operations. This technique is especially useful in environments where data needs to be shared for testing or analytics without exposing actual sensitive information. Masked data can be used in non-production environments, reducing the risk of data breaches during development or analysis.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) are critical for monitoring network traffic and identifying potential security threats in real-time. These systems use a combination of signature-based and anomaly-based detection methods to identify suspicious activity, such as unauthorized access attempts or unusual data transfer patterns. Once a potential threat is detected, the IDPS can take immediate action to block or mitigate the attack, thereby preventing data breaches and minimizing damage.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) solutions are designed to prevent sensitive data from being leaked, either intentionally or unintentionally, outside the organization. DLP systems monitor data transfers across networks, email, and other communication channels, ensuring that confidential information does not leave the organization without proper authorization. DLP protocols are particularly important in financial services, where regulatory compliance and data privacy are critical concerns.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying and addressing vulnerabilities within financial institutions’ IT systems. Security audits involve reviewing and assessing the effectiveness of existing security measures, while penetration testing simulates real-world attacks to evaluate the robustness of the institution’s defenses. By conducting these assessments regularly, financial institutions can stay ahead of potential threats and ensure that their security protocols are up to date and effective.
Compliance with Regulatory Standards
Financial institutions are subject to a range of regulatory requirements aimed at protecting customer data and ensuring the integrity of financial systems. Compliance with standards such as the General Data Protection Regulation (GDPR), the Payment Card Industry Data Security Standard (PCI DSS), and the Gramm-Leach-Bliley Act (GLBA) is not only a legal obligation but also a critical component of a comprehensive data security strategy. Adhering to these regulations ensures that financial institutions implement best practices for data protection and reduces the risk of regulatory fines and penalties.
The Role of Employee Training
While advanced security technologies are crucial, human factors remain a significant vulnerability in data security. Social engineering attacks, such as phishing, often exploit human error to gain access to sensitive information. To mitigate this risk, financial institutions must invest in regular employee training programs that educate staff about security best practices, the latest threat trends, and the importance of maintaining a security-first mindset. Empowering employees to recognize and respond to potential security threats is a vital component of a holistic data security strategy.
Conclusion
In the financial services industry, data security is not just a technical challenge but a business imperative. As cyber threats continue to evolve, financial institutions must remain vigilant and proactive in their approach to data security. By implementing robust security protocols, staying compliant with regulatory standards, and fostering a culture of security awareness, financial institutions can effectively mitigate risks and protect their most valuable asset: data. Ensuring the confidentiality, integrity, and availability of financial data is essential for maintaining customer trust and safeguarding the future of the industry.
Read Whitepaper Data Dilemmas: Solving Financial Services Challenges
